Release 5.0.0 - OpalOPC is now Free and Open Source

- Licensing removed
- Telemetry removed
- Source published


You are the producer of a component with an OPC UA interface. You want to certify it to IEC 62443-4-2 using ISASecure CSA or ICSA schemes.
Before you can do that, you must certify its development process to IEC 62443-4-1 using ISASecure SDLA. To achieve the SDLA certificate, you must demonstrate that you follow the 8 security practices defined in the IEC 62443-4-1 standard.

OpalOPC now supports the SARIF output format in version 3.2.0.0. This enhancement allows seamless integration with other tools that also use SARIF, such as GitHub Advanced Security. By adopting SARIF, you gain a unified view of your security posture.
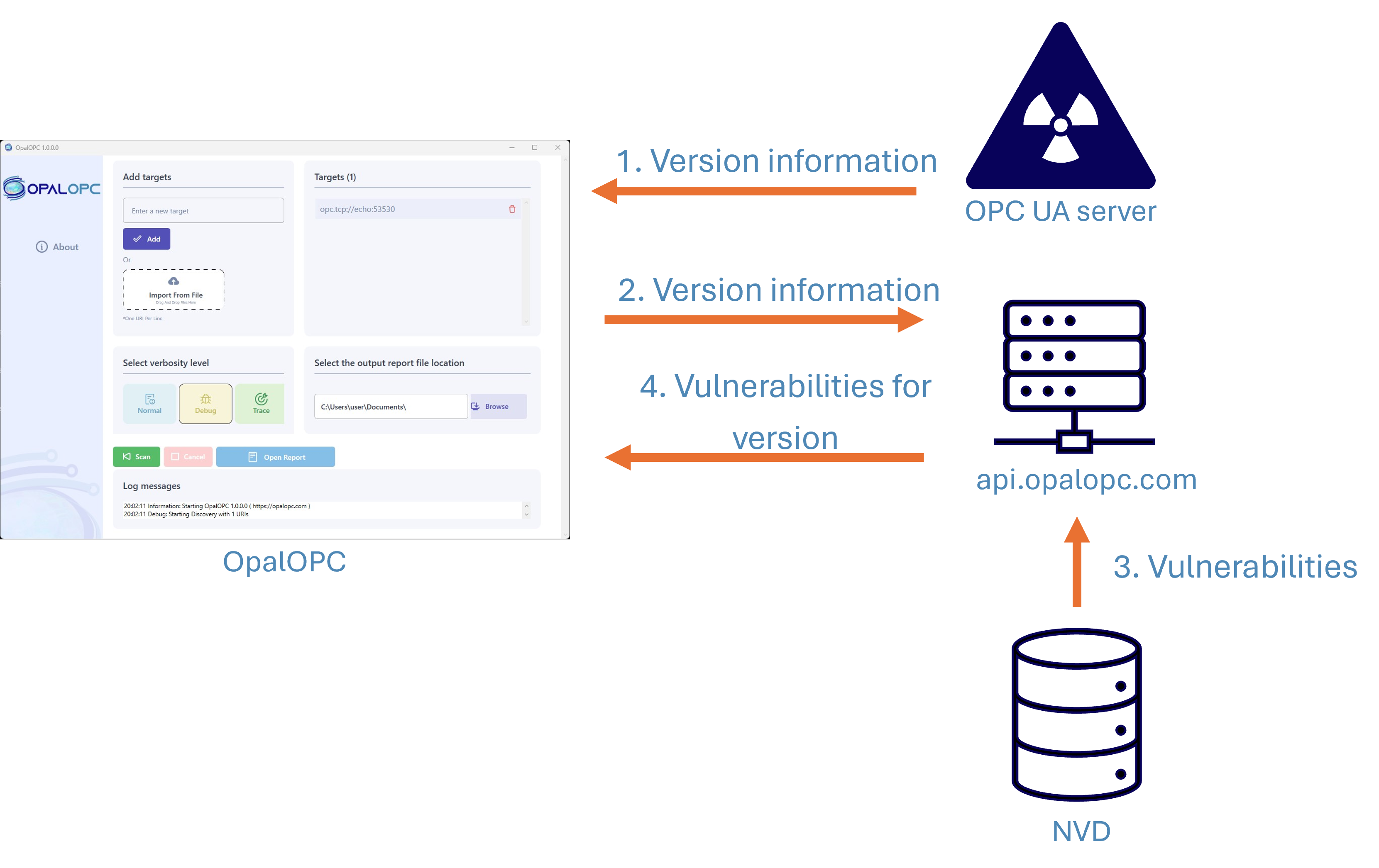
Starting from version 3.1.0.0, OpalOPC detects publicly known vulnerabilities. If your target is running OPC UA server software with associated vulnerabilities in the National Vulnerability Database, they will be included in the scan report.


View my presentation on hands-on hacking of OPC UA.

Starting from OpalOPC 2.0.3.0, the Linux installer has been replaced by Snap. This makes it easy for Linux users to install and keep the scanner up-to-date. Furthermore, the security features of Snap protect our customers when installing, updating, or using our product.
